
By: Probrand
Every year Probrand highlights how the cybersecurity threat is increasing, because protecting data and systems is a priority for organisations. But with cybercriminals working constantly to find and exploit any weakness in systems or people, and releasing new threats, it’s difficult to keep up-to-date so you can prioritise your cybersecurity efforts. So, let’s take a look at what happened in 2020 and what that means for your cybersecurity priorities in 2021.
How it started
2020 began and ended with two historic events: the COVID-19 pandemic and the discovery of the SolarWinds supply-chain attack. The pandemic brought global disruption unlike anything seen in generations, fundamentally changing the way we worked, the way we shopped, and how we interacted with each other. The SolarWinds attack was revealed in December and struck the IT world at it’s very centre, triggering a series of events that would impact thousands of organisations, lifting the veil on a type of breach immune to virtually all current defences.
During this period cybercriminals scaled up their efforts to take advantage of the current conditions: the rise of remote working, cryptocurrency prices rising to record levels, a charged political climate, and threat actors weaponising cloud infrastructure and tools – all of which they used to drive the effectiveness and volume of attacks to a new high.
As usual, the attacks focussed on where they saw vulnerabilities and a high likelihood of success; remote workers unaware of the additional risks when outside the corporate network, essential and overwhelmed healthcare facilities, schools and universities trying to deliver a curriculum remotely and ensure students could stay on track.
SonicWall Capture Labs threat researchers tracked these developments, which are all combined into the 2021 SonicWall Cyber Threat report. Here’s a brief overview of what they discovered:
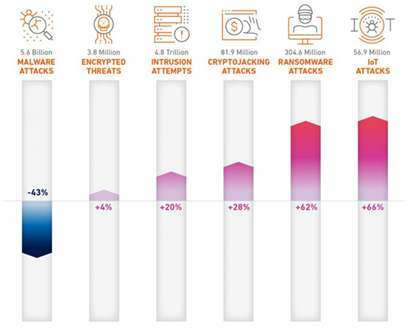
Top-level insights
- Record levels of ransomware attacks and cryptojacking linked to record highs in the price of Bitcoin and other cryptocurrency.
- Rapid growth in use of newer Ryuk family of ransomware that continues to gain new capabilities.
- Sharp increase in ransomware attacks targeted at healthcare organisations.
- The pandemic accelerated the adoption of IoT devices which increased IoT malware attacks by 66%.
- Malicious intrusion attempts jump 112% overall — but the nature of these attacks also changed. Directory Traversal attempts jumped from 21% to 34% of total malicious attempts, while RCE attempts lost steam, falling from 21% to 16%.
What does this mean for me?
In 2019 most organisations had the majority of devices on-site within the network with security and updates handled by the IT team. But the rush to survive in 2020 prioritised remote access to systems over robust cybersecurity measures, and the sudden rush on laptop stock (and continued shortages) meant some fell back to letting users access the network via personal devices and often poorly secured Wi-Fi routers. This has created an expanding and less secure cyber attack surface, a fact that cybercriminals have been quick to take advantage of.
The majority of these attacks follow similar patterns and there are some simple tactics you can undertake like enabling multi-factor authentication and ensuring you have the appropriate firewall for your circumstances which will reduce your risk and protect your people, data and reputation.
The majority of these attacks follow similar patterns and there are some simple tactics you can undertake like enabling multi-factor authentication and ensuring you have the appropriate firewall for your circumstances which will reduce your risk and protect your people, data and reputation.
How can I protect my business?
Getting a cybersecurity certification for your business is a good way to stand out from the pack and show potential customers and business partners that you’ve done your security homework. But which should you get?
Cyber Essentials
Perhaps the most relevant cybersecurity certification for small businesses in the UK is the government’s own Cyber Essentials scheme. Operated by the UK National Cyber Security Centre (NCSC), it’s a certification in good practice for cybersecurity.
Cyber Essentials offers two levels of certification. The first, Cyber Essentials, is a self-assessment option that demonstrates you’re competent in five areas of technical controls: firewalls, secure configuration, user access control, malware protection, and security update management.
In this option, companies fill out an online questionnaire, and then a board member signs a declaration to confirm that all the information given is true. An assessor then checks over the answers and makes a decision.
This online questionnaire is also a requirement for the second, higher level of certification, known as Cyber Essentials Plus. Within three months of taking the questionnaire, you can apply for a hands-on technical audit from an accredited auditor working with the NCSC.
Other accreditations
Cyber Essentials is a good all-round basic cybersecurity hygiene certification, but other certifications take a more general view of cybersecurity controls. ISO 27001 focuses more on information management. It looks at areas ranging from risk assessment and security policy through to asset management, physical security, and human resources security. It also examines issues such as access control and incident management. As a broader information security certification with many more moving parts, it is likely to take significantly more time and work, both to prepare and to get assessed.
Some cybersecurity and information security accreditations are industry requirements rather than voluntary projects. One example is the Payment Card Industry Data Security Standard (PCI-DSS) created by the Payment Card Industry Standards Council, an independent body organized by payment payment card companies.
PCI-DSS carries different levels of accreditation based on which type of merchant you are. That in turn is determined by criteria such as how many credit card transactions you process and how you take payments. This accreditation requires a mixture of regular automated vulnerability scans and possibly an on-site audit depending on your company’s characteristics.
Why get certified?
When a set of industry partners demands certification, you don’t have a choice. When it’s a voluntary system, you’ll weigh the time and cost of certification against three main factors:
- Reputation: Sporting a certification can go a long way towards building trust in your company before you even begin building a relatioship with a customer. They can be a valuable marketing asset when building your industry brand.
- Compliance: A certification might be a requirement for some customers, especially those in heavily regulated industries. Doing all this groundwork now can avoid costly headaches later when a customer lists certification as a requirement on its RFP or sales contract.
- Peace of mind: Going through the certification process is also an excellent way to refine and improve your own cybersecurity and information management controls. Even if you are never asked to produce this, it will make you more confident that you’re offering a mature, safe service to your customers.


