
By Jonathan Maresky, Cloud Product Marketing Manager at Check Point Software
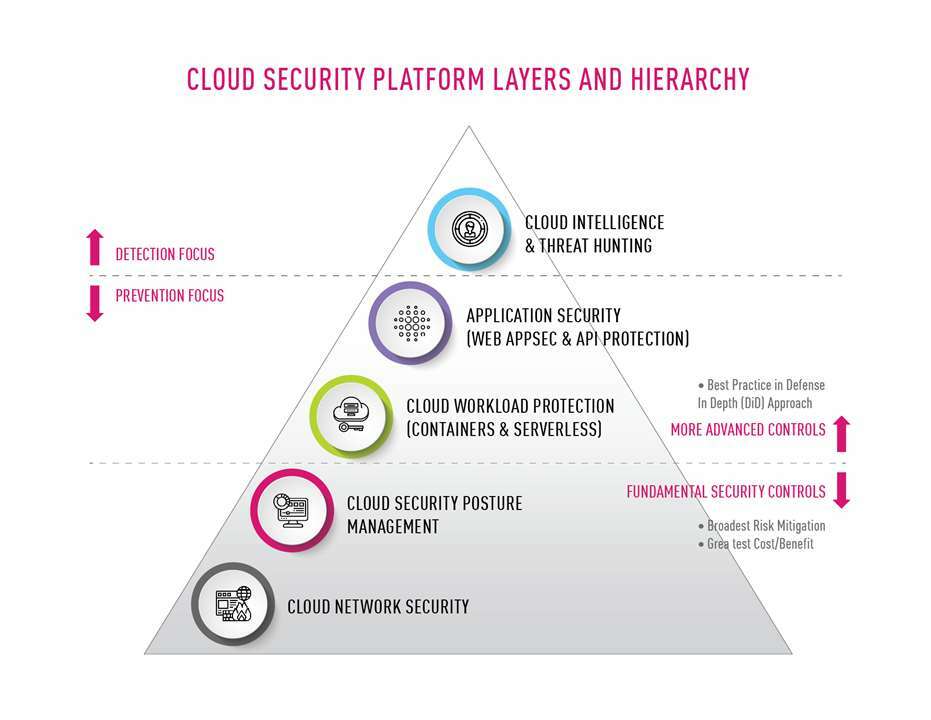
Cloud security has become business-critical as organizations expand and deepen their cloud presence. According to the Check Point 2020 Cloud Security Report, 75% of surveyed organizations were either very or extremely concerned about cloud security. The figure below illustrates the kind of multilayered yet unified cloud security platform that organizations should put in place in order to protect their cloud deployments and ensure a robust cloud security posture. Similarly, a recent Forrester study stated that cloud security confidence is a leading driver for adopting more cloud services.
Figure 1: The Multiple Layers of a Unified Cloud Native Security Platform
It is always important to remember that cloud security takes place in the context of a shared responsibility model. At the infrastructure level (IaaS), cloud providers are responsible for securing their compute-network-storage infrastructure resources while users are responsible for protecting the data, apps, and other assets deployed on the infrastructure. The tools and services offered by cloud providers to help users uphold their end of the shared responsibility model are important elements of any cloud network security solution. However, cloud providers are not specialists in security; these cloud provider tools and services must be complemented by partner solutions in order to achieve enterprise-grade network security.
As shown in figure 1, a key foundational layer is cloud network security, where organizations should deploy virtual security gateways to provide advanced threat prevention, traffic inspection and micro-segmentation. Such security solutions use multiple layered security technologies including Firewall, IPS, Application Control, DLP and others.
This article describes the ten essential considerations a company should examine when choosing its cloud network security platform. It explains how you can ensure that vendor solutions have the capabilities that are important to your organization’s success and security.
In order to match the speed and scalability of DevOps, the solution must support high levels of automation, including programmatic command and control of security gateways, seamless integration with CI/CD processes, automated threat response and remediation workflows, and dynamic policy updates that don’t require human intervention.
The total cost of ownership is determined by a number of factors, all of which should be considered as part of the buying process: the flexibility of the licensing model, the extent to which the cloud security platform seamlessly integrates with and leverages existing IT systems, the level and scope of personnel required to administer the system, the vendor’s MTTR and availability SLAs, and more. You want your cloud security platform to streamline operations, optimize workflows, and reduce costs while enhancing your security posture. The last thing you want is to be surprised by hidden infrastructure, personnel and other costs that emerge only after the system is up and running.
Organizations are increasingly moving to the cloud to meet business demands. These organizations want the ability to control their own data and keep it private, protect themselves from cyber threats and securely connect their cloud with their traditional on-premises network, all while maintaining compliance with regulatory mandates. Adopting a cloud network security solution that meets these requirements will help organizations remain protected in an increasingly complex threat environment.


